Market Snapshot
| Indices | Week | YTD |
|---|
The World was abuzz last week with news that President Trump had accepted Kim Jong-Un’s (a.k.a. “Rocket Man”) invitation to discuss de-nuking North Korea. While it’s obviously scary to imagine enemies of the Red, White, and Blue having nuclear weapons, focusing on atoms is so 20th Century.
Building walls, having security guards watch safes, and having police patrol our communities are the realities of a dangerous World. But the clear and present danger is invisible and digital.
With over three billion people on the Internet and two billion smartphones, the hyper-connected World we live in has great opportunities and perilous risk. EVERYTHING is now connected — from our financial system, to telecommunications, utilities, defense, and automobiles. You name it and it’s “1’s” and “0’s” that make everything work.
Using physical cash already seems quaint, with one-third of Americans and one-fifth of Europeans going cashless according to ING. Global e-commerce platforms like Amazon and Alibaba are making physical currencies less relevant. In 2003, the Global e-commerce industry recorded revenues of $70 billion. By 2006, it doubled to $136 billion, and by 2016, it had grown over 10x to $1.9 trillion. By 2021, e-commerce is expected to reach $4.5 trillion.
This modern digital system is fantastic if used for good. But if utilized for evil, the consequences are catastrophic. And while it’s unclear the motive or source of many cyberattacks, it is clear that no one is safe.
Russia has been at the epicenter of major cyberhacks, with the Russians hacking elections, hacking the Internet, hacking the Olympics, and hacking the World. This year logged the biggest cryptocurrency hack when Japanese cryptocurrency exchange Coincheck lost more than $500 million worth of coins overnight. Even the Securities and Exchange Commission — the poster child for secured regulation — was hacked in 2017, granting hackers access to inside information about companies.
In the past few years, 3 billion Yahoo accounts were hacked and half of the U.S. population was affected by Equifax’s hack, which leaked names, birth dates, addresses, and social security numbers to the public. 57 million Uber accounts were compromised. Russian cyberhacker “Peace” stole passwords from 350 million MySpace, 117 million LinkedIn, 70 million Twitter, and 65 million Tumblr accounts.
Funny enough, just having a smarter password would eliminate a significant amount of cyber thievery. For example, according to SplashData, the number one password is “123456,” which nearly 3% have used. An estimated 10% of people have used at least one of the top 25 worst passwords. Ironically, the 25th most used password is “trustno1”.

The greatest investment opportunities are where there is a problem. The greater the problem, the greater the opportunity. In our hyper-connected World, digital crime is a burgeoning problem, and hence, a massive opportunity for companies that offer Cybersecurity solutions.
STATE OF PLAY
2014 was marked by two watershed moments in Cybersecurity. First is the now infamous Sony Pictures Entertainment hack where 6,000 employees showed up for work to learn that their computers had been compromised. Troves of personal data were stolen. Emails were made public. Movies were released. Amy Pascal, then Co-Executive Chairman, remembers frantically calling down to IT, imploring, “Please tell me that they don’t have my emails.” “They” did. Pascal was later fired after her salty appraisals of actors, directors, and peers went public.
As with Financial and Technology companies, Media companies like Sony have long been completely dependent on their digital infrastructure and have been among the most aggressive adopters of Cybersecurity products. What’s amazing about the breach is that Sony was running the very best security systems and they still got whacked like a Piñata in front of the whole World.
The second key moment was the hacking of the U.S. Office of Personnel Management, where 22 million detailed personal records of Federal employees were stolen. Captured data included background checks, fingerprints, and more. Ultimately attributed to Chinese hackers, the breach sent a shocking message to the World. No institution — not even the formidable U.S. Government — is beyond the reach of Cyber crime.
And while it seemed that the worst is over, the storm had only begun. In 2017, Yahoo announced that all 3 billion of Yahoo’s users had been compromised, dating back to a hack in 2013. MySpace’s owner Time revealed in May 2016, that 360 million MySpace accounts was hacked in 2013. Equifax’s claim to shame was the loss of sensitive information of 146 million Americans.

Financing Activity
Cybersecurity is poised for strong growth because threats are multiplying and the risk of failure can destroy a business. Demand is surging across sectors, from banks and retailers to government agencies and hospitals. Gartner predicts that worldwide spending on information security technology will grow to $93 billion in 2018. But this is likely an understatement because firms are not making incremental purchasing decisions.
Importantly, cyberattacks will continue to accelerate, so company budgets for Cybersecurity spending will grow independently of the broader economy. VCs have taken notice and are accelerating investment activity.
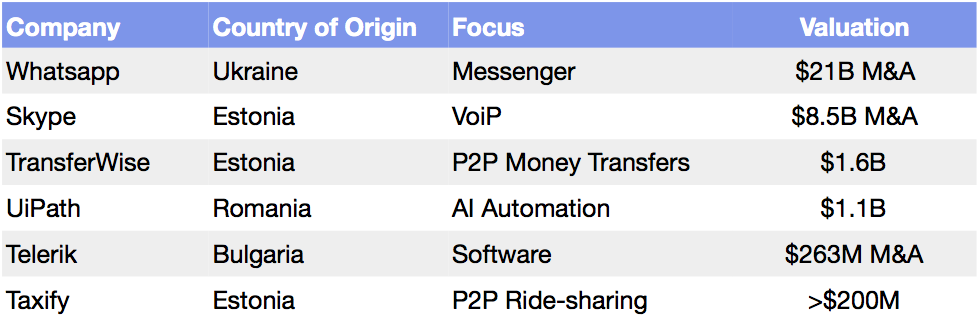
2017 was a record year for Cybersecurity startups which raised a combined $7.7 billion venture funding according to CB Insights, more than double the amount raised in 2016. In 2017, there were 10 companies raising mega-round financings of over $100 million, including Skybox Security ($150 million), Illumio ($125 million), Tanium ($100 million), and CrowdStrike ($120 million).
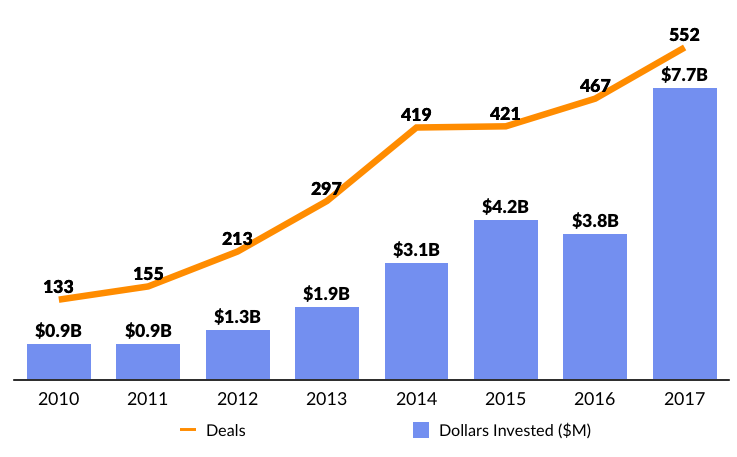

Source: CB Insights
CB Insights identified “Monitoring and Security” as the largest category for 2018 IPO candidates, with 24 companies in the pipeline. In total, the sector has produced 10 Unicorns, which have raised $1.8 billion and combined is valued at $13 billion.

CALL TO ARMS: CYBERSECURITY STARTUPS
Cybersecurity stalwarts like Symantec (founded: 1982) and Juniper Networks (founded: 1996) came of age at the dawn of the digital era in a finite world of cyber threats. Modern day Cybersecurity startups leverage powerful digital technologies and infrastucture to detect, monitor and resolve threats. Cylance, for example, uses machine learning and pattern recognition to predict and thwart new malware attacks.
Today, a wave of new companies is emerging founded by entrepreneurs that are targeting risk and vulnerabilities that didn’t exist ten years ago.
Corporate + Enterprise
In the first half of 2017 alone, almost 2 billion data records cross the World were stolen by cyberattacks. According to digital security provider Gemalto, the two-thirds of affected firms had their share price negatively affected. All in all, over $52 billion of shareholder value was wiped out across 65 firms due to cyberattacks.
As the pace of cyberattacks keeps on increasing, corporations are struggling to keep up in maintaining the security of their digital assets and platforms.
As corporations seek to shore up security deficiencies, two types of services are emerging to meet demand. For businesses with more sophisticated defenses and capable tech talent, companies like Lookout and Illumio offer specialized protection focused on certain types of threats or aimed at safeguarding mobile devices (e.g. network “endpoints,” such as smartphones and tablets).
For businesses with a broader need to create World-class security infrastructure, companies like Veracode and AlienVault offer all-in-one Cybersecurity platforms to meet corporate security requirements at once.

Source: CB Insights, Crunchbase, GSV Asset Management
Other companies like HackerOne offer services to help customers build programs to detect vulnerabilities in their software. HackerOne’s bug bounty platform lets companies offer money to security experts to detect softness in the code which could be prone to outside attacks. Founded in 2012, the San Francisco-based company has raised $74 million from investors including Benchmark, Dragoneer, NEA, Drew Houston and Marc Benioff.
This January, Alphabet launched its latest moonshot Chronicle, dubbed by Google X Head Astro Teller as a “digital immune system.” Chronicle’s focus is to detect threats by analyzing and storing security-related data within enterprises. Using Google’s vast infrastructure, the platform is equip to detect threats faster and at a broader scale than existing offerings.
Cloud
Until recently, corporations could rely on a cyber defense strategy akin to digging a moat around a castle. The standard security perimeter was a firewall and extended with a Virtual Private Network (VPN).
But today, companies are rapidly adopting cloud services like Dropbox, Zendesk, Salesforce, and Box. The digital infrastructure that powers these services — as well as troves of related data, permissions, and settings — is no longer behind the “moat.” Absent new defenses, in other words, corporate castles are vulnerable. (Disclosure: GSV owns shares in Dropbox)
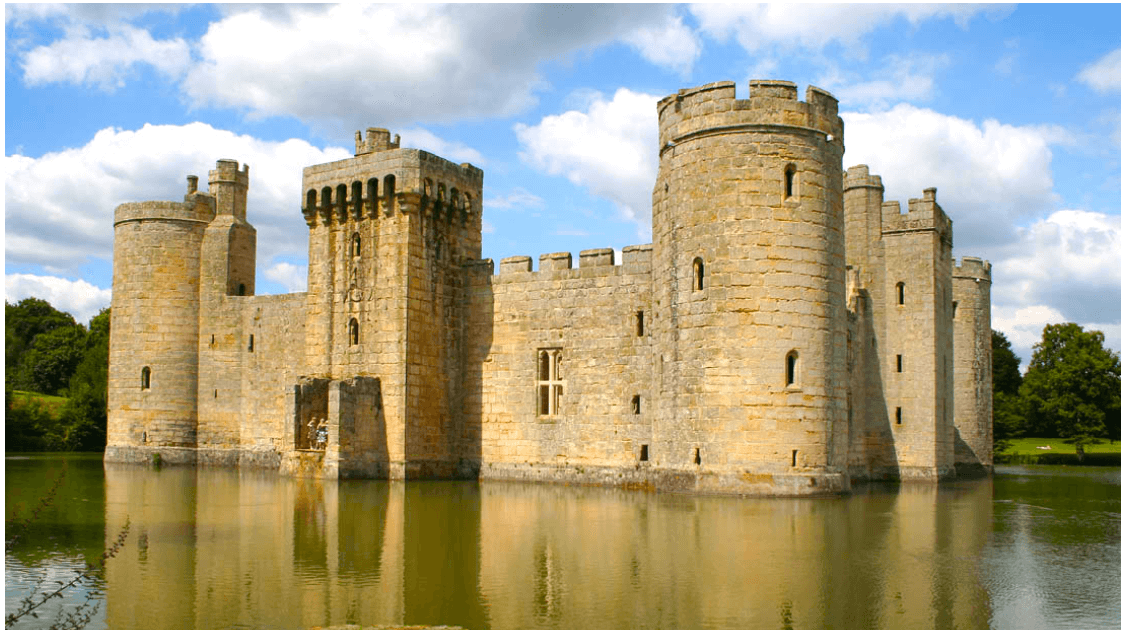
The net result has been two-fold. First, companies no longer control the digital domain where their employees operate. For example, to create or deactivate the account of a help desk professional, a company needs to manage all of those settings in Zendesk.
The second key impact is that as companies integrate widely adopted cloud-based services into their IT stack, the potential for problems to multiply is massive. If Box, which serves over 50,000 corporations with 39 million employees, were to be compromised, the impact would be widespread.
Companies like Ciphercloud and Elastica provide Cybersecurity solutions specifically focused on secure access to cloud-based applications from anywhere. This is becoming increasingly important with the use of cloud-housed services and applications.

Personal + Fraud Protection
Now more than ever, personal data is vulnerable to abuse. In the past few years, 3 billion Yahoo accounts were hacked and half of the U.S. population was affected by Equifax’s hack, which leaked names, birth dates, addresses, and social security numbers to the public. 57 million Uber accounts were compromised. Russian cyberhacker “Peace” stole passwords from 350 million MySpace, 117 million LinkedIn, 70 million Twitter, and 65 million Tumblr accounts.
A final category of Cybersecurity businesses are focused on protecting consumers and battling fraud. Companies like Psafe Technologies and Wickr help consumers secure their mobile devices and personal data. Companies like FeedZai and EyeVerify are focused on thwarting identity theft and fraud.

Despite innovations in personal security and fraud prevention, consumers continue to suffer from a lack of security accountability across the critical digital infrastructure they use every day. Take the process of making an online purchase with a credit card as an example.
While it appears to be a simple transaction to the end user, the process actually includes up to five parties: Consumer, E-Commerce Company (e.g. Amazon), Bank (e.g. Bank of America), Transaction Processor (e.g. First Data), and the Credit Card company (e.g. Visa). The division of accountability for various cyber breaches among these key parties still remains alarmingly ambiguous. There will be much litigation before this is resolved.
WHAT’S NEXT
The first few generations of Cybersecurity companies led to creation of companies leveraging digital technology infrastructure to provide Cybersecurity solutions protecting all types of customers, ranging from an individual to large enterprises. Moving forward, we see key areas for the emergence of additional Cybersecurity blockbusters.

If nuclear wars and cyber wars weren’t bad enough, President Trump brought a trade war back into play by promising tariffs on countries exporting steel to the United States. That was enough for Economic advisor Gary Cohn to bolt and for Markets to have a temporary heart attack.
Perhaps after recalling that President Reagan was a protectionist in his early presidency — he hit Japanese Semiconductors with a 100% tariff tax and excluded Canada and Mexico from being penalized — Markets ripped upwards. Fuel was put on the fire with huge job growth. The most positive bit of news was that people were actually going back to find jobs as opposed to quit looking, which was the case over the past 10 years.
NASDAQ was up 4.2% for the week reaching an all time high, and the S&P 500 advanced 3.5% for the week. Good news continues for growth investors, and the forthcoming strong IPO Market should provide oxygen to the Bulls.